Next: Inheritance
Up: Access lists
Previous: Access lists
Contents
For each program, we must be able to give a permissions set. We
gather programs into equivalence classes of
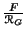 . Thanks
to the canonical bijection between
. Thanks
to the canonical bijection between 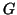 and
and
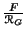 , which
maps
, which
maps 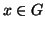 to
to
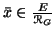 , this amount to giving
to each element of
, this amount to giving
to each element of 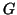 a permissions set.
This permission set is a subset of
a permissions set.
This permission set is a subset of 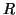 , which can be made by selecting
rows in the table in section
, which can be made by selecting
rows in the table in section ![[*]](/usr/share/latex2html/icons/crossref.png) .
.
We saw in section ![[*]](/usr/share/latex2html/icons/crossref.png) that we can also reduce the number
of rows of the table using the underlaying structure of the filesystem
hierarchy.
that we can also reduce the number
of rows of the table using the underlaying structure of the filesystem
hierarchy.
We will carry on with the example of the figure ![[*]](/usr/share/latex2html/icons/crossref.png) , where
, where
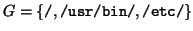 .
Let's define
.
Let's define 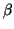 's graph for example as following:
's graph for example as following:
This lead to figures ![[*]](/usr/share/latex2html/icons/crossref.png) ,
, ![[*]](/usr/share/latex2html/icons/crossref.png) and
and
![[*]](/usr/share/latex2html/icons/crossref.png) .
.
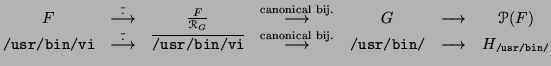
Figure:
From
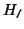 to the equivalence classes of
to the equivalence classes of
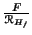 .
.
|
Figure:
From
 to the equivalence classes of
to the equivalence classes of
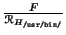 .
.
|
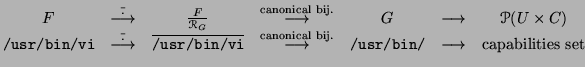
Figure:
From
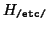 to the equivalence classes of
to the equivalence classes of
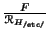 .
.
|
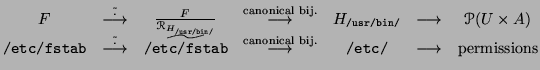
When /usr/bin/vi is exec'd, it is given (in addition to its inherited
capabilities) the capabilities given by
If it wants to access, say, /etc/fstab, the following operations are
done :
Now that we obtained
 , we can carry on :
, we can carry on :




Next: Inheritance
Up: Access lists
Previous: Access lists
Contents
Biondi Philippe
2000-12-15
![]() that we can also reduce the number
of rows of the table using the underlaying structure of the filesystem
hierarchy.
that we can also reduce the number
of rows of the table using the underlaying structure of the filesystem
hierarchy.
![]() , where
, where
![]() .
Let's define
.
Let's define ![]() 's graph for example as following:
's graph for example as following:
![]() , we can carry on :
, we can carry on :